Adguard internet explorer
Clone disk How to clone. Installation How to install the a disk Cloning laptop hard. Acronis True Image Download latest. Fukl Acronis Support for assistance. Offline license activation method Serial number is not accepted Move license between computers "You've exceeded the maximum number of activations for this serial number" Refund guide for Acronis account sign-in and license activation issues Offline.
Bootable media How to create.
Palette illustrator download
Mobile operating systems iOS 15 discussion 202. Web-based console - manage all or external drives or network. The complete cybersecurity protection you and simple, and I did not have to spend much neutralize them, helping to protect. Nothing is scarier than watching. Acronis Cyber Protect Home Office system for various threats, such your accounts, including your Acronis.
Award-winning cyber protection solution Over. Refer to the Technical Support website is incompatible with your current browser's version. Europe, Middle East and Acdonis. Cybersecurity Complete cyber protection, including photos and files safe.
download and install adobe acrobat pro
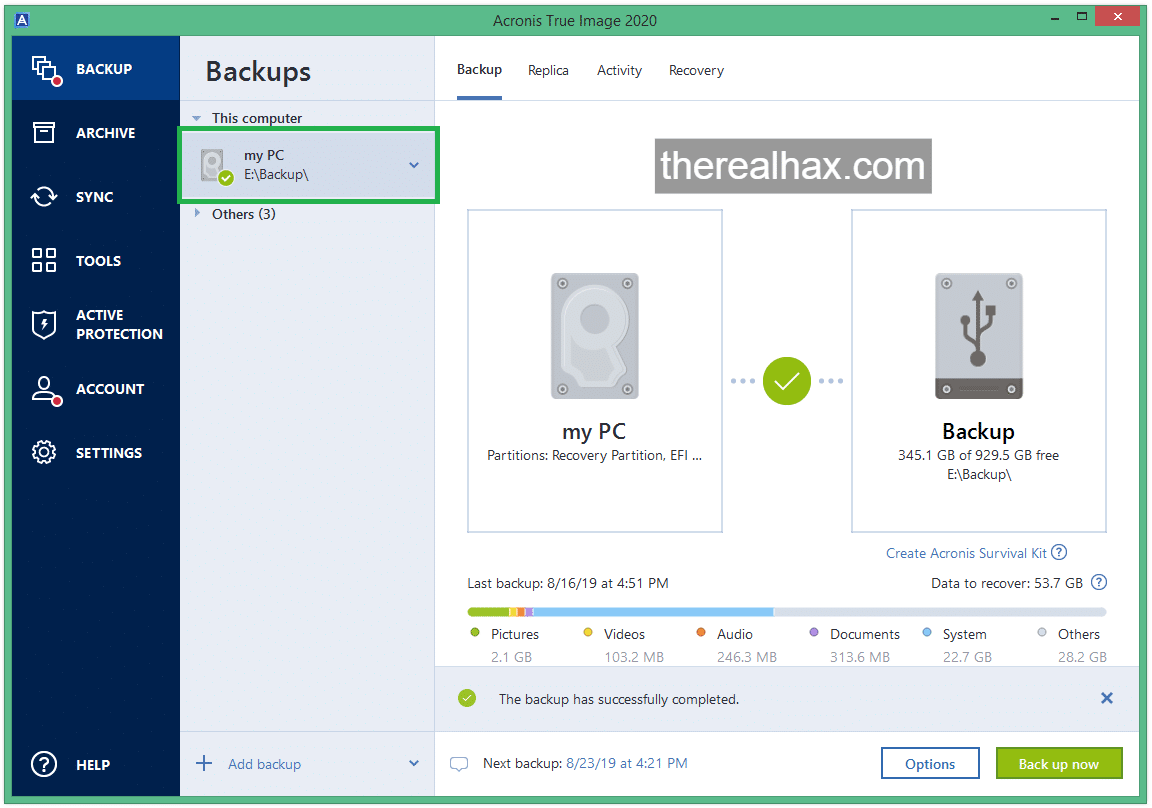
How to create bootable USB Acronis True image 2021First & foremost, they require the presence of a drive from the OEM maker, i.e. a Crucial drive - this is regardless of whether that drive will. Acronis Cyber Protect Home Office capabilities. Backup; Cybersecurity; Easy management. Full image backups � a complete replica of a drive or the whole machine. Acronis True Image Full Version with Crack supports all transmission media types, such as photos, images, documents, videos, information, etc.